It is very simple to configure automatic backup of a recovery password in pure server environment. If you have clients then you will probably want to configure self-service portal to get recovery passwords (or at least delegation for Service Desk) but in server environment it is usually enough to use default configuration that only Domain Admins have access to recovery passwords.
Group Policy
Secure Trusted Platform Module (TPM)
The TPM Owner Password defines who the owner of the TPM is. You own the TPM if you are able to set the TPM Owner Password. Only one owner password exists per TPM, so anyone who knows that password is effectively the TPM owner. The owner of the TPM can make full use of TPM capabilities. Once an owner is set, no other user or software can claim ownership of the TPM.
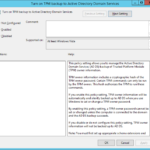
- First you need to ensure that TPM Owner Password cannot change.
Configuration for testing environment
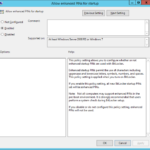
- For testing environment you also need to be able to activate BitLocker in any protectors including password protector for example on virtual machines without TPM.
- Windows Components\BitLocker Drive Encryption\Operating System Drives
- Require additional authentication at startup
- Allow BitLocker without a compatible TPM (requires a password or a startup key on a USB flash drive):Enabled
- Settings for computers with a TPM:
- Configure TPM startup: Allow TPM
- Configure TPM startup PIN: Allow startup PIN with TPM
- Configure TPM startup key: Allow startup key with TPM
- Configure TPM startup key and PIN: Allow startup key and PIN with TPM
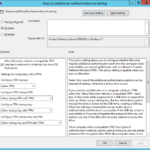
- Windows Components\BitLocker Drive Encryption\Operating System Drives
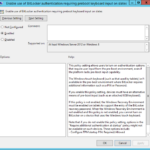
Configure backup to AD DS
- Setting that will enforce backup to Active Directory…
- Computer Configuration\Policies\Administrative Templates\Windows Components\BitLocker Drive Encryption\Operating System Drives
- Choose how BitLocker-protected operating system drives can be recovered
- Allow data recovery agent: Enabled
- Configure user storage of BitLocker recovery information:
- Allow 48-digit recovery password
- Allow 256-bit recovery key
- Omit recovery options from the BitLocker setup wizard: Disabled
- Save BitLocker recovery information to AD DS for operating system drives: Enabled
- Configure storage of BitLocker recovery information to AD DS: Store recovery passwords and key packages
- Do not enable BitLocker until recovery information is stored to AD DS for operating system drives: Enabled
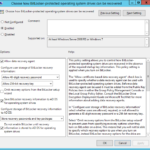
- Choose how BitLocker-protected operating system drives can be recovered
- Computer Configuration\Policies\Administrative Templates\Windows Components\BitLocker Drive Encryption\Operating System Drives
- There are a similar settings in:
- Computer Configuration\Policies\Administrative Templates\Windows Components\BitLocker Drive Encryption\Fixed Data Drives
- Computer Configuration\Policies\Administrative Templates\Windows Components\BitLocker Drive Encryption\Removable Data Drives
Another interesting configurations
- This will allow you to use any characters (not only digits) in PIN:
- And this will allow you to input text on devices without hardware keyboard (for example on your Microsoft Surface tablet):
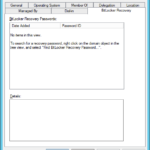
View recovery passwords that are stored in AD
At this point when you encrypt new volume then recovery password is securely transfer (protected by using Kerberos authentication protocol) to Active Directory. Recovery password are stored in plain text but without delegation there are visible only to Domain Admins.
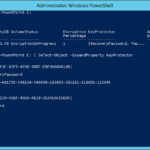
Install BitLocker Remote Server Administration Tools (RSAT) on your management server
- PowerShell
Install-WindowsFeature -Name RSAT-Feature-Tools-BitLocker -IncludeAllSubFeature -Verbose
Get-WindowsFeature -Name RSAT*bitlo*
<#
Display Name Name Install
State
------------ ---- ----------
[X] BitLocker Drive Encryption Administration Utilities RSAT-Feature-Tools-BitLocker Installed
[X] BitLocker Drive Encryption Tools RSAT-Feature-Tools-BitLocker-RemoteAdminTool Installed
[X] BitLocker Recovery Password Viewer RSAT-Feature-Tools-BitLocker-BdeAducExt Installed
#>
- Then you can check that there is a new tab BitLocker Recovery in Active Directory Users and Computers (ADUC).
- Of course it is visible in Active Directory Admistrative Center too.
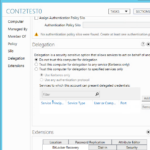
- Now you can enable BitLocker and check the protectors. You can also see Password protector because cont2test0.ad1.contoso.com computer is a testing virtual machine.
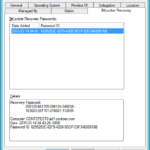
- And when you check BitLocker Recovery tab in ADUC then you will see a new record.

2 responses to “How to manage and configure BitLocker Drive Encryption – Group Policy and backup and restore to and from Active Directory”
This is amazing. Thank you! Question, it looks like the keys aren’t saving to AD. bitlocker is enabled on the test machine but when i try to backup the machine to AD via powershell with (manage-bde -protectors -adbackup c:) I get the following error ERROR: Group policy does not permit the storage of recovery information to Active Directory. The operation was not attempted. Thanks for your help!
@Victor: Computer Config -> Admin Templates -> Windows Components -> BitLocker Drive Encryption -> "Store BitLocker recovery information in Active Directory…" Enable.